Blue Team Training Toolkit (BT3) is software for defensive security training, which will bring your network analysis training sessions, incident response drills and red team engagements to a new level.
BT3 includes Mocksum, which is a module that allow you to simulate and plant realistic artifacts during training sessions, incident response drills or red team engagements.
This blog post is going to cover the most fundamental aspects of Mocksum that will get you started in no time.
Mocksum – Simulate and Plant Realistic Artifacts
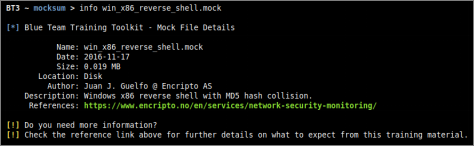
Mocksum is a module that provides access to a collection of files that mimic malware samples via MD5 hash collisions. The files downloaded via Mocksum allow you to simulate and plant realistic artifacts during training sessions, incident response drills or red team engagements. Without the risk of handling real malware. In a nutshell, these artifacts are harmless files that produce the same MD5 checksum as real malicious files. In many cases, the harmless artifacts also get detected by anti-virus software.
The Most Relevant Commands
- Invoking Mocksum
The module can be invoked with “use mocksum” directly from the BT3 command-line interface. You should note that the BT3 command prompt changes based on the current module in use.
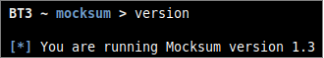
- Module version check
The current module version can be checked with the “version” command.
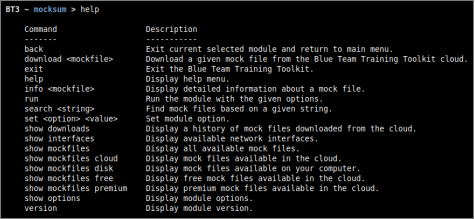
- Module help overview
Mocksum supports a range of general commands, which can be displayed with “help”.
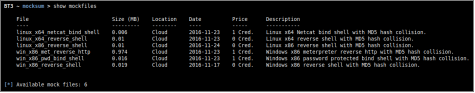
- Module material list
Mock files available for use can be listed with “show mockfiles”. If a content subscription account is already authenticated, the command will retrieve mock file information from the online library. More targeted mock file listing can be achieved with “show mockfiles cloud”, “show mockfiles disk”, “show mockfiles free” and “show mockfiles premium”. These commands will present all mock files available online, mock files found locally on your computer, mock files which can be downloaded for free, and mock files which can be downloaded with the use of content credits respectively.
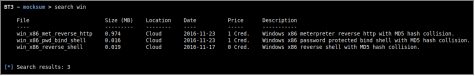
- Material search
Available mock files can be easily found with the “search” command. Searches use the mock file name or its description as criterion.
- Material information
Detailed information about a given mock file can be shown with the “info” command. The expected command argument is the mock file to present. Note that mock files downloaded to your local disk will have a “.mock” extension, while those online do not.
- Material download
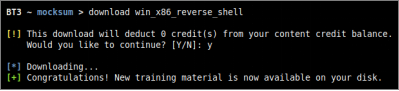
Authenticated content subscription accounts will have access to the Blue Team Training Toolkit online library, with both free and premium training content. Premium online training content has a price, which will be deducted from the user’s existing content credit balance. Premium downloads require users to have enough credit balance in order to complete the download. Free online content, on the other hand, can be downloaded without restrictions. Downloading online resources can be done with the “download” command, and the material name provided as an argument.
- Material download history
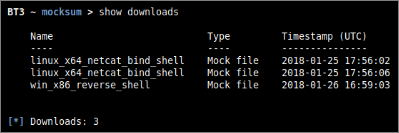
The training material download history associated with your subscription account can be retrieved with “show downloads”.
- Module network interfaces overview
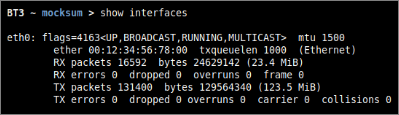
Available network interfaces can be displayed with the “show interfaces” command. This has been included in order to provide a more homogeneous command list among the different BT3 modules.
- Module option list
This module currently provides access to the mock file library and it has no configurable options.
- Module execution
This module currently provides access to the mock file library and it cannot be run.
Next Steps
Once a mock file has been downloaded to your disk, you may plant it in your training environment. Multiple possibilities and goals can be accomplished with mock files, such as:
- Flags
Mock files could be used as flags, which let the blue team know that a (simulated) malicious file has been found.
- Mastering log correlation and third party threat intelligenceMock files have MD5 hash collisions that mimic real malware samples. By calculating their checksums, your blue team can find real information about the mimicked malware sample in different sources. This kind of practice can allow the blue team to master event investigation, get used to using third party threat intelligence services, or correlate in-house logs (e.g. Centralized anti-malware solution).
For a more realistic experience, mock files can be renamed to “.exe” (Windows) or “.bin” (Linux). Since the mock files are not malicious files, there is no risk if the files are accidentally executed.
Check out the BT3 user guide, or the Blue Team Training Toolkit Video Series for practical examples.
You can also download the Blue Team Training Toolkit and test it for yourself!