Blue Team Training Toolkit (BT3) is software for defensive security training, which will bring your network analysis training sessions, incident response drills and red team engagements to a new level. The toolkit allows you to create realistic computer attack scenarios, while reducing infrastructure costs, implementation time and risk.
This blog post is going to cover the BT3 module Maligno, which allows you to simulate malware infections or targeted attacks with specific C&C communications in a safe manner. Multiple malware indicator profiles ensure a “plug & play” experience.
Adversary Replication and Malware Simulation
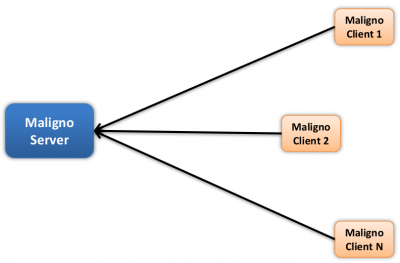
Maligno is designed for attack simulations that require risk-free / fictive malware infections, or targeted attacks with specific C&C communications. The module follows a client-server architecture, where the server component is hosted by the same computer where BT3 is running, and the client component can be deployed on different machines if desired.
Currently, Maligno server is integrated in the Blue Team Training Toolkit, and it runs on any of the supported operating systems covered in the system requirements section. However, Maligno clients can run on any operating system (e.g. Microsoft Windows, or Linux) as long as Python 2.7 is installed. Maligno clients can also run on Windows when compiled with PyInstaller. At the moment, client-server communications are handled via HTTP or HTTPS, since these are two of the most popular protocols used by malware these days.
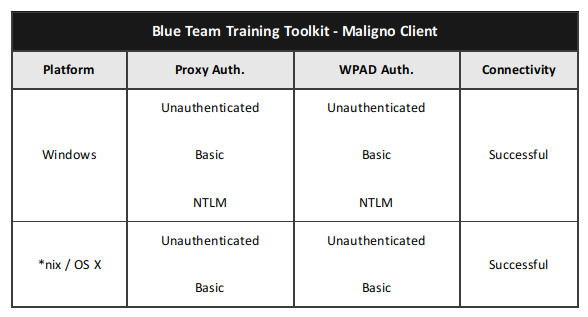
Maligno clients are proxy aware, and they can handle themselves in multiple environments. Different proxy capabilities have been implemented in Maligno clients so far. These capabilities depend on what operating system a Maligno client is running on. The table listed below summarizes what connection scenarios are possible on different client platforms.
Check out the BT3 user guide, or the Blue Team Training Toolkit Video Series for practical examples.
You can also download the Blue Team Training Toolkit and test it for yourself!