Blue Team Training Toolkit (BT3) is software for defensive security training, which will bring your network analysis training sessions, incident response drills and red team engagements to a new level.
BT3 includes Pcapteller, which is a module designed for network traffic manipulation and replay. It allows organizations to re-create a recorded network traffic scenario that occurred in a foreign network, as it really happened in their own infrastructure.
This blog post will demonstrate how Pcapteller can be used during a simple training session.
Practical Example
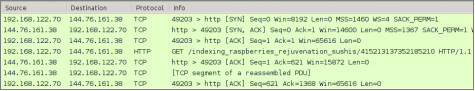
This case will use a public PCAP file that contains an attack scenario involving an exploit kit delivering ransomware. This PCAP file describes a chain of events where host “192.168.122.70” is the victim.
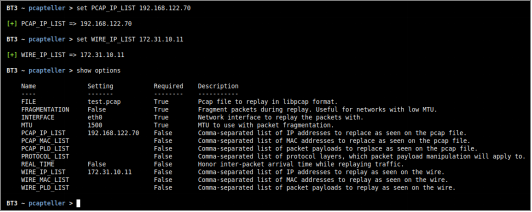
Let’s consider an organization that would like to use such resource for a training session. The organization is interested in using its current security countermeasures and configurations in production. The production network is using a class B internal IPv4 addressing schema (172.31.0.0/16). For this example, the victim machine will become “172.31.10.11”. In this case, the following module options should be configured:
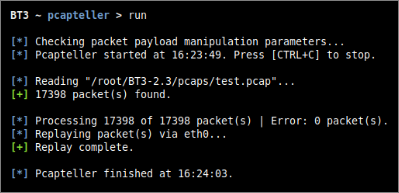
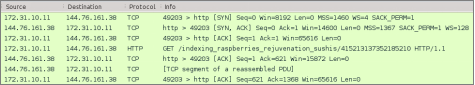
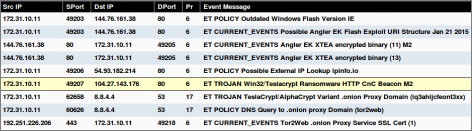
The result of the customized traffic injected into the network is described in the screenshots below.
Since Pcapteller injects the manipulated network traffic into the production network, existing security countermeasures can detect and alert about possible threats. This example shows how an Intrusion Detection System (Snort with ET GPL ruleset) would react to the manipulated traffic.
Check out the BT3 user guide, or the Blue Team Training Toolkit Video Series for practical examples.
You can also download the Blue Team Training Toolkit and test it for yourself!