Blue Team Training Toolkit (BT3) is software for defensive security training, which will bring your network analysis training sessions, incident response drills and red team engagements to a new level. The toolkit allows you to create realistic computer attack scenarios, while reducing infrastructure costs, implementation time and risk.
This blog post is going to cover the most fundamental aspects of Blue Team Training Toolkit (BT3) that will get you started in no time.
Download and Installation
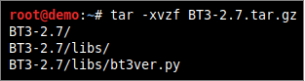
Blue Team Training Toolkit is distributed as a tarball file. Once the file is on your hard disk, proceed to extract it and run the installer as shown below.
Please, note that the screenshots are illustrative. Make sure you type folder and file names correctly (according to your downloaded BT3 tarball and final deployment folder), as the folders and file names shown by the screenshots may not fit your environment.
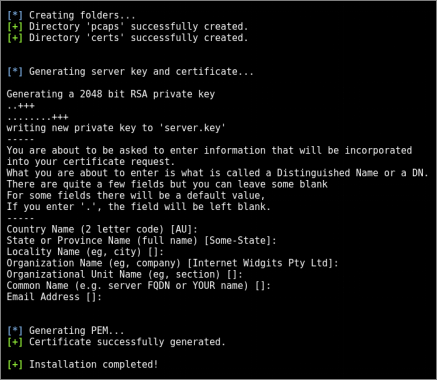
During the installation process, the installer will proceed to create a self-signed server certificate that can be used with BT3’s Maligno module. The certificate generation process will require some information. At this point of the installation, you will have the opportunity to use default values by pressing “Enter”, or providing your own. Be aware default values could trigger IDS signatures under certain circumstances.
As soon as the certificate is generated, the installer will place it in the “certs” folder. You may add extra certificates (PEM format) to this folder for later use, if desired. At this point, the installation process should be complete.
Check out the BT3 user guide, or the Blue Team Training Toolkit Video Series for practical examples.
You can also download the Blue Team Training Toolkit and test it for yourself!